Works
This portfolio provides a glimpse into some of the impactful projects I've led and delivered throughout my career. While I can't disclose confidential details, I'm happy to discuss my experiences and expertise in more general terms. If you see potential for collaboration or have any questions, please don't hesitate to reach out.

HMI/Scada Tool Development

Threat Analysis and Risk Assessment Tool Development
Modular Threat Catalog
Security Assessment for Automated Driving Software
Security Library Development

Security Assessment of Multi Purpose Camera

Security Concept for Multi Purpose Camera

360° Surround View ECU Development
Security Assessment Over-the-Air Update Solution
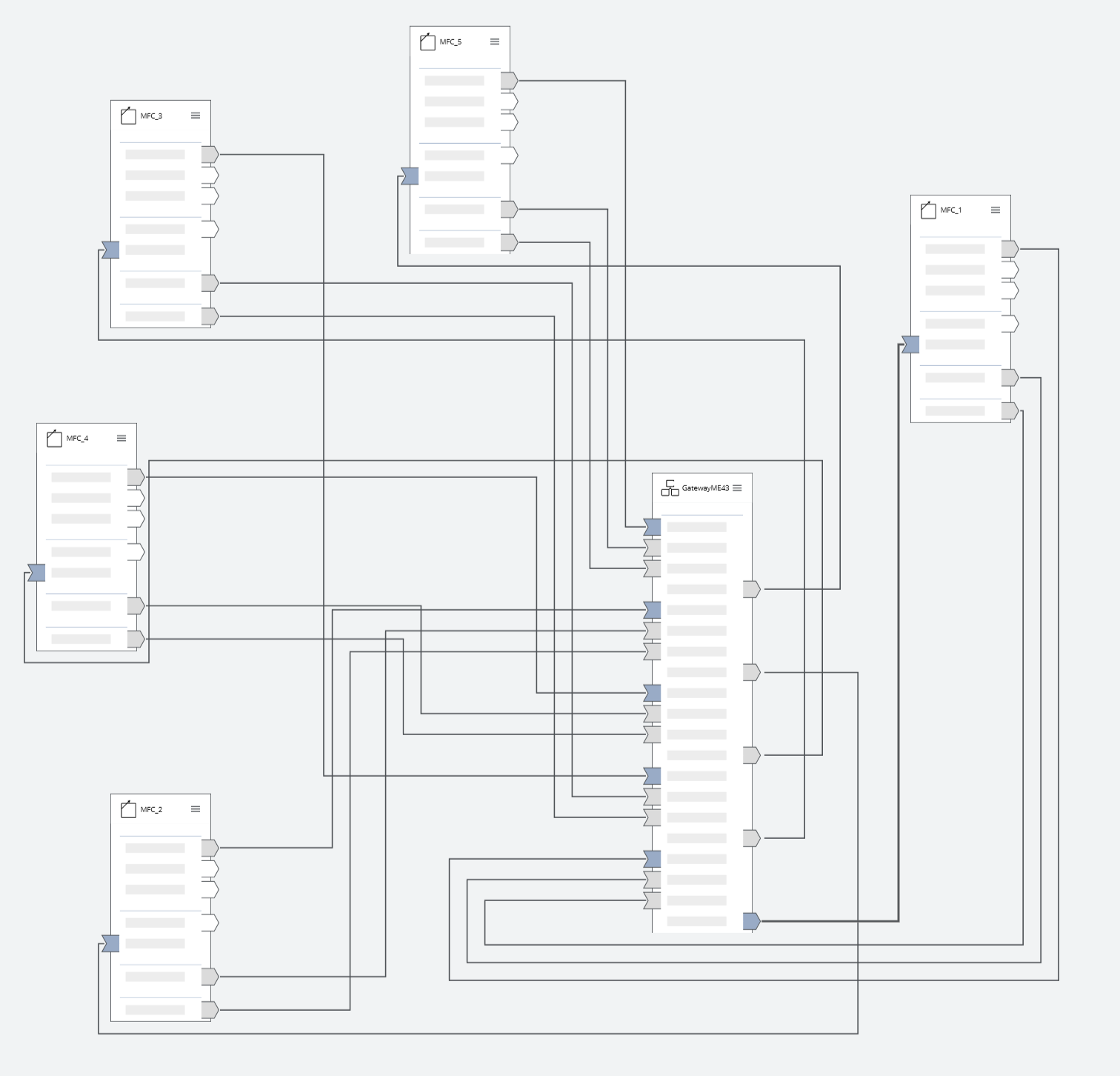
Graphical Producer Consumer Configuration
Need Some Answers?
Embedded Security Assessment?
Embedded systems are computer systems that are integrated into a specific technical context. Typical tasks of embedded systems are monitoring or controlling as well as data and signal processing in the context of larger mechanical or electrical systems. While embedded systems are commonly used in industrial areas, they are becoming more and more prevalent in consumer products (e.g., in the smart home area) and often are equipped with connections to internal networks or the Internet. In this context, the terms Internet of Things (IoT) or cyber-physical systems (CPS) are often used to describe the connectivity of everyday objects.
Penetration Test?
Vulnerabilities in IT or embedded systems can have serious consequences for many companies. If, for example, entire production plants and critical infrastructures fail as a result of a successful attack, significant economic damage can occur in a very short time. The threat scenarios and effects for a company are very individual. This also applies to security assessments of IT environments or of individual components. With a penetration test, I offer you a targeted review of IT environments or individual components, taking into account individual threat scenarios. The objective of a penetration test is, in particular, the assessment of existing risks with regard to specific threat scenarios. A statement should also be made as to what an attacker can achieve in the worst case within a limited time window.
What is you Penetration Test Process?
As part of a penetration test, targeted attack vectors are defined based on specific threat scenarios. These are then included in the penetration test and simulated by our specialized employees. Depending on the perspective (external, internal, privileged user), scenario and objective, network components, servers, applications or clients, among other things, are included in the attack attempts. Based on the given threat scenarios, individual IT systems are first analyzed in detail for weak points. Subsequently, specific attacks are carried out on the systems via the identified vulnerabilities in order to achieve the set goals either directly or by exploiting other subsequent vulnerabilities.
Differences to Red Teaming?
This is more like a real-world attack simulation. The "red team" acts like real attackers, using various tactics to breach your defenses over a longer period. They try to stay hidden and achieve specific goals, like accessing sensitive data. This helps you understand how well your security works against determined adversaries and identify gaps in your detection and response capabilities. Here is a simple analogy: Imagine your company is a house. A penetration test is like checking the locks on your doors and windows to make sure they're secure. A red team assessment is like having someone try to break into your house while you're away, testing your alarm system, security cameras, and your ability to respond to the intrusion. Both are valuable for improving your security, but a red team assessment provides a more comprehensive and realistic picture of your overall security posture.
Can you build me a website?
Yes, for sure. I can do this (and successfully did in the past). But the REAL question is if you want me to do that.